Area: Orientation
Objectives
Holiday Hack Orientation
Difficulty: 1/5 Christmas Trees
Description: Talk to Jingle Ringford on Christmas Island and get your bearings at Geese Islands
Dialog
Jingle Redford
Welcome to the Geese Islands and the 2023 SANS Holiday Hack Challenge!
I'm Jingle Ringford, one of Santa's many elves.
Santa asked me to meet you here and give you a short orientation to this festive event.
Before you head back to your boat, I'll ask you to accomplish a few simple tasks.
First things first, here's your badge! It's that starfish in the middle of your avatar.
Great - now you're official!
Click on the badge on your avatar. That's where you will see your Objectives, Hints, and Conversations for the Holiday Hack Challenge.
We've also got handy links to some awesome talks and more there for you!
Next, pick up that fishing pole over there in the sand. That will come in handy when you're sailing around the islands.
Solution
Picked up Fishing Pole item as requested.
Jingle Ringford
Fantastic!
OK, one last thing. Click on the **Cranberry Pi Terminal**and follow the on-screen instructions.
Typed answer in the terminal to solve.
Unlocked achievement.
Congratulations! You have completed the Holiday Hack Orientation challenge!
Jingle Ringford
Perfect! Your orientation is now complete!
Head back to your boat or click on the anchor icon on the left of the screen to set sail for Frosty's Beach where Santa's waiting for you. I've updated your boat's compass to guide the way.
As you sail to each island, talk to the goose of that island to receive a colorful lei festooning the masts on your ship.
Safe travels my friend and remember, relax, enjoy the sun, and most importantly, have FUN!
Area: Frosty's Beach
Dialog
Goose of Christmas Island
Honk honk
Santa
Welcome to the Geese Islands, fellow traveler! This one is called Christmas Island. Nooo ho ho, not _that_Christmas Island.
After countless years of shivering and shaking through each holiday season, I thought to myself, "Why not trade the snowflakes for sunbeams, just once?"
Oh, the North Pole has its charm, but the bones do yearn for a bit of warmth now and then.
The notion was suggested by my good friend, Chat North Pole Technology, or as we like to call it, 'ChatNPT'. That's the one we use, but there's a whole slew of other AI platforms. You should try them out!
It came to me describing palm trees and gentle waves, saying, "Santa, let your holidays take flight to Geese Islands, where the warmth isn't just a setting."
"There, every day is a sunny scene straight out of a vintage film reel."
I chuckled at the thought, my belly shaking like a bowl full of jelly.
But the AI persisted, "Winter's best kept secret: the balmy breezes of Geese Islands!"
And I must confess, the sound of that did stroke my beard with curiosity.
So, I called a meeting with the elves, the reindeer, and Mrs. Claus, of course.The elves were all a-buzz with the idea of crafting toys with a view of the ocean!
Thus, we packed up our sleighs and ChatNPT charted a course for the Geese Islands, a tropical paradise just north of the equator..
And I must say, there's something quite magical about a Christmas carol sung to the strum of a ukulele.
After all, the magic of the holidays isn't in the snow or the cold, but in the love and the care that we put into each and every gift.
So here's to trying new things, to following the sunshine, and to the Geese Islands, where the holiday cheer is sun-kissed and the Christmas spirit is as warm as the tropical breeze.
And it's all thanks to a little nudge from ChatNPT.
Now, why not start off your vacation with a snowball fight with Morcel, or check out my surf shack on the other end of the beach?
However you decide to relax, be sure to soak in all the whimsical beauty of these magical islands, and enjoy the activities to the fullest!
After completing both objectives:
Congratulations! You are a true snowball fight champion and thank you so much for helping out Ginger Breddie!
Oh, it feels like the warm and gentle winds are starting to pick up!
The perfect time to head back to your boat and embark on an adventure to all the other whimsical places the Geese Islands have to offer!
Safe travels my friend and thank you again for your help!
Hints
Santa: Synthesis Is The True Ending
The AI revolution has begun. Some of the most prominent and useful tools born from the advent of powerful AI include ChatGPT, PlayHT, Midjourney, Dall-E 3, Bing AI, and Bard, and Grok.
Objective: Snowball Fight
Difficulty: 2/5 Christmas Trees
Description: Visit Christmas Island and talk to Morcel Nougat about this great new game. Team up with another player and show Morcel how to win against Santa!
Dialog
Morcel Nougat
Hey there, I'm Morcel Nougat, elf extraordinaire!
You won't believe this, but we're on a magical tropical island called Christmas Island, and it even has snow!
I'm so glad ChatNPT suggested we come here this year!
Santa, some elves, and I are having a snowball fight, and we'd love you to join us. Santa's really good, so trust me when I say it's way more fun when played with other people.
But hey, if you can figure out a way to play solo by tinkering with client side variables or parameters to go solo mode, go for it!
There's also ways to make the elves' snowballs do no damage, and all kinds of other shenanigans, but you didn't hear that from me.
Just remember, it's all about having fun and sharing the joy of the holiday season with each other.
So, are you in? We'd really love your company in this epic snowball battle!
After completing Snow Ball Fight:
You're like a snowball fighting ninja! A real-life legend. Can I have your autograph!?
Hints
Consoling iFrames From: Morcel Nougat Terminal: Snowball Hero
Have an iframe in your document? Be sure to select the right context before meddling with JavaScript.
Snowball Super Hero From: Morcel Nougat Terminal: Snowball Hero
Its easiest to grab a friend play with and beat Santa but tinkering with client-side variables can grant you all kinds of snowball fight super powers. You could even take on Santa and the elves solo!
Solution
Open the terminal, then open the Dev Tools in your browser. Make sure the correct iFrame context is selected. The following screenshot shows the context selection menu in the Console tab of Firefox's Dev Tools.
Create a private room. You will initially be shown instructions for the game.
Santa and his whimsical elves challenge thee to a snowball duel in their snow arena! Only a snowball of matching color can banish an elf, so choose your targets with care!

As for Santa, the jolly old soul, only a dual-strike from both thine hands, within a breath's span, shall chip his icy shield! When you're ready to face the frosty foes, smite the 'Ready' button below and let the snowball saga commence!
(use your mouse to throw and the arrow keys to move)
The game will never start because there is not a second player. While investigating the JavaScript code we discover that a single player mode should exist in the game, but there does not appear to be any way to initiate this mode.
var singlePlayer = "false"
function checkAndUpdateSinglePlayer() {
const localStorageValue = localStorage.getItem('singlePlayer');
if (localStorageValue === 'true' || localStorageValue === 'false') {
singlePlayer = String(localStorageValue === 'true');
}
const urlParams = new URLSearchParams(window.location.search);
const urlValue = urlParams.get('singlePlayer');
if (urlValue === 'true' || urlValue === 'false') {
singlePlayer = String(urlValue === 'true');
}
When investigating the GET requests fired off when entering a new private room a singlePlayer request parameter as shown below is discovered.
/ws/?username=borari&roomId=49bc68e1&roomType=private&gameType=co-op&id=0aa0aaaa-aaaa-aaaa-aaaa-fa0000000000&dna=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA&pos=1025-1049&singlePlayer=false
We set a Burp Match and Replace rewrite rule to match singlePlayer=false and replace it with singlePlayer=true, resulting in the new URI of:
/ws/?username=borari&roomId=49bc68e1&roomType=private&gameType=co-op&id=0aa0aaaa-aaaa-aaaa-aaaa-fa0000000000&dna=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA&pos=1025-1049&singlePlayer=true
I also made the following match and replace rules for the response body in order to make the game significantly easier.
var elfThrowDelay = 2000 // var elfThrowDelay = 9999
var snowballDmg = 2 // var snowballDmg = 999
var playersHitBoxSize = [30,30,40,60] // var playersHitBoxSize = [1,1,1,1]
var elfHitBoxSize = [32,32,48,48] // var elfHitBoxSize = [99,99,99,99]
var santaHitBoxSize = [60,60,70,70] // var santaHitBoxSize = [99,99,99,99]
var santaThrowDelay = 500 // var santaThrowDelay = 9999
After playing the game and defeating Santa, a video plays describing the amazing feat, and the Snowball Fight achievement pops.
Congratulations! You have completed the Snowball Fight challenge!
Area: Santa's Surf Shack
Objective: Linux 101
Difficulty: 1/5 Christmas Trees
Description: Visit Ginger Breddie in Santa's Shack on Christmas Island to help him with some basic Linux tasks. It's in the southwest corner of Frosty's Beach.
Dialog
Ginger Breddie
Hey, welcome to Santa's Surf Shack on tropical Christmas Island! I'm just hanging ten here, taking it easy while brushing up on my Linux skills.
You ever tried getting into Linux? It's a super cool way to play around with computers.
Can you believe ChatNPT suggested this trip to the Geese Islands this year? I'm so thrilled!
Kudos to ChatNPT, eh? The sunshine, the waves, and my surfboard – simply loving it!
So, what do you have planned? Care to join me in a Linux session?
After completing challenge:
Wow, if your surfing skills are as good as your Linux skills, you could be winning competitions!
Solution
Open the Linux 101 CranberryPi terminal.
The North Pole 🎁 Present Maker:
All the presents on this system have been stolen by trolls. Capture trolls by following instructions here and 🎁's will appear in the green bar below. Run the command "hintme" to receive a hint.
Perform a directory listing of your home directory to find a troll and retrieve a present!
elf@88c3cc386717:~$ ls -lAh
total 52K
-rw-r--r-- 1 elf elf 28 Dec 2 22:19 .bash_history
-rw-r--r-- 1 elf elf 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 elf elf 3.1K Nov 20 18:04 .bashrc
-rw-r--r-- 1 elf elf 807 Feb 25 2020 .profile
-rw-r--r-- 1 elf elf 168 Nov 20 18:04 HELP
-rw-r--r-- 1 elf elf 24 Dec 2 22:19 troll_19315479765589239
drwxr-xr-x 1 elf elf 24K Dec 2 22:19 workshop
Now find the troll inside the troll.
elf@88c3cc386717:~$ cat troll_19315479765589239
troll_24187022596776786
Great, now remove the troll in your home directory.
elf@88c3cc386717:~$ rm troll_19315479765589239
Print the present working directory using a command.
elf@88c3cc386717:~$ pwd
/home/elf
Good job but it looks like another troll hid itself in your home directory. Find the hidden troll!
elf@88c3cc386717:~$ ls -lAh
total 48K
-rw-r--r-- 1 elf elf 28 Dec 2 22:19 .bash_history
-rw-r--r-- 1 elf elf 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 elf elf 3.1K Nov 20 18:04 .bashrc
-rw-r--r-- 1 elf elf 807 Feb 25 2020 .profile
-rw-r--r-- 1 elf elf 0 Dec 13 16:34 .troll_5074624024543078
-rw-r--r-- 1 elf elf 168 Nov 20 18:04 HELP
drwxr-xr-x 1 elf elf 24K Dec 2 22:19 workshop
Excellent, now find the troll in your command history.
elf@88c3cc386717:~$ history | grep troll
1 echo troll_9394554126440791
3 cat troll_19315479765589239
4 rm troll_19315479765589239
7 history | grep troll
Find the troll in your environment variables.
elf@88c3cc386717:~$ env
...
HOSTNAME=88c3cc386717
RESOURCE_ID=ac4ac1e8-3f8f-4cf7-a276-bbd1104014b7
GREENSTATUSPREFIX=presents
PWD=/home/elf
LOGNAME=elf
SESSNAME=Troll Wrangler
z_TROLL=troll_20249649541603754
HOME=/home/elf
LANG=C.UTF-8
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.wim=01;31:*.swm=01;31:*.dwm=01;31:*.esd=01;31:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:
HHCUSERNAME=borari
AREA=cisantassurfshack
BPUSERHOME=/home/elf
LESSCLOSE=/usr/bin/lesspipe %s %s
TERM=screen
LESSOPEN=| /usr/bin/lesspipe %s
USER=elf
TOKENS=
TMUX_PANE=%2
BPUSER=elf
SHLVL=3
LC_ALL=C.UTF-8
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
MAIL=/var/mail/elf
LOCATION=7,5
_=/usr/bin/env
Next, head into the workshop.
elf@88c3cc386717:~$ cd workshop
A troll is hiding in one of the workshop toolboxes. Use "grep" while ignoring case to find which toolbox the troll is in.
elf@88c3cc386717:~/workshop$ grep -i "troll" ./*.txt
./toolbox_191.txt:tRoLl.4056180441832623
A troll is blocking the present_engine from starting. Run the present_engine binary to retrieve this troll.
elf@88c3cc386717:~/workshop$ chmod +x ./present_engine
elf@88c3cc386717:~/workshop$ ./present_engine
troll.898906189498077
Trolls have blown the fuses in /home/elf/workshop/electrical. cd into electrical and rename blown_fuse0 to fuse0.
elf@88c3cc386717:~/workshop$ cd /home/elf/workshop/electrical
elf@88c3cc386717:~/workshop/electrical$ la
total 4.0K
-rw-r--r-- 1 elf elf 200 Dec 2 22:19 blown_fuse0
elf@88c3cc386717:~/workshop/electrical$ mv blown_fuse0 fuse0
Now, make a symbolic link (symlink) named fuse1 that points to fuse0.
elf@88c3cc386717:~/workshop/electrical$ ln -s fuse0 fuse1
Make a copy of fuse1 named fuse2.
elf@88c3cc386717:~/workshop/electrical$ cp fuse1 fuse2
We need to make sure trolls don't come back. Add the characters "TROLL_REPELLENT" into the file fuse2.
elf@88c3cc386717:~/workshop/electrical$ echo "TROLL_REPELLENT" >> fuse2
Find the troll somewhere in /opt/troll_den.
elf@edf6125dfed1:/opt/troll_den$ find "troll" . | more
.
./bundles
./bundles/admin
./bundles/admin/src
...
./plugins/portlet-mocks/src/test/java/org/apache/t_r_o_l_l_2579728047101724
...
Find the file somewhere in /opt/troll_den that is owned by the user troll.
elf@edf6125dfed1:/opt/troll_den$ ls -lAhR . | grep troll
-rw-r--r-- 1 root root 1.2K Dec 2 22:19 IndexController.java
-rw-r--r-- 1 root root 3.5K Dec 2 22:19 OrdersController.java
-rw-r--r-- 1 troll troll 0 Dec 2 22:19 tr0LL_9528909612014411
-rw-r--r-- 1 root root 23K Dec 2 22:19 ParserController.java
Find the file created by trolls that is greater than 108 kilobytes and less than 110 kilobytes located somewhere in /opt/troll_den.
elf@edf6125dfed1:/opt/troll_den$ ls -lAhR | grep -e 108 -e 109 -e 110
total 108K
total 108K
-rw-r--r-- 1 root root 108 Dec 2 22:19 README.md
-rw-r--r-- 1 root root 109K Dec 2 22:19 t_r_o_l_l_2579728047101724
-rw-r--r-- 1 root root 109 Dec 2 22:19 README.md
List running processes to find another troll.
elf@edf6125dfed1:/opt/troll_den$ ps -aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
init 1 0.0 0.0 20112 16268 pts/0 Ss+ 17:09 0:00 /usr/bin/python3 /usr/local/bin/tmuxp load ./mysession.yaml
elf 7254 0.2 0.0 31520 26612 pts/2 S+ 17:21 0:00 /usr/bin/python3 /14516_troll
elf 7968 0.0 0.0 7672 3224 pts/3 R+ 17:22 0:00 ps -aux
The 14516_troll process is listening on a TCP port. Use a command to have the only listening port display to the screen.
elf@edf6125dfed1:/opt/troll_den$ netstat -antup
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:54321 0.0.0.0:* LISTEN 7254/python3
The service listening on port 54321 is an HTTP server. Interact with this server to retrieve the last troll.
elf@edf6125dfed1:/opt/troll_den$ curl 127.0.0.1:54321
troll.73180338045875
Your last task is to stop the 14516_troll task to collect the final presents.
elf@edf6125dfed1:/opt/troll_den$ ps -aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
init 1 0.0 0.0 20112 16268 pts/0 Ss+ 17:09 0:00 /usr/bin/python3 /usr/local/bin/tmuxp load ./mysession.yaml
elf 7254 0.0 0.0 105616 27168 pts/2 S+ 17:21 0:00 /usr/bin/python3 /14516_troll
elf 10117 0.0 0.0 7672 3128 pts/3 R+ 17:26 0:00 ps -aux
elf@edf6125dfed1:/opt/troll_den$ kill 7254
Finishing this challenge unlocked the Linux 101 Achievement!
Congratulations! You have completed the Linux 101 challenge!
Area: Rudolf's Rest
Dialog
Goose of Christmas Island
Honk honk
Hints
Objective: Reportinator
Difficulty: 2/5 Christmas Trees
Description: Noel Boetie used ChatNPT to write a pentest report. Go to Christmas Island and help him clean it up.
Dialog
Noel Boetie
Intro
Hey there, Noel Boetie speaking! I recently tried using ChatNPT to generate my penetration testing report.
It's a pretty nifty tool, but there are a few issues in the output that I've noticed.
I need some guidance in finding any errors in the way it generated the content, especially those odd hallucinations in the LLM output.
I know it's not perfect, but I'd really appreciate the extra eyes on this one.
Some of the issues might be subtle, so don't be afraid to dig deep and ask for further clarification if you're unsure.
I've heard that you folks are experts about LLM outputs and their common issues, so I trust you can help me with this.
Your input will be invaluable to me, so please feel free to share any insights or findings you may have.
I'm looking forward to working with you all and improving the quality of the ChatNPT-generated penetration testing report.
Thanks in advance for your help! I truly appreciate it! Let's make this report the best it can be!
Hint
I know AI sometimes can get specifics wrong unless the prompts are well written. Maybe chatNPT made some mistakes here.
After Solving
Great job on completing that challenge! Ever thought about how your newfound skills might come into play later on? Keep that mind sharp, and remember, today's victories are tomorrow's strategies!
Solution Attempt
Click the CranberryPi terminal to launch the challenge iFrame. It consists of a website containing a Penetration Test Report, with the following instructions.
Report Conventions
(Green Checkmark) This icon represents a legitimate finding. Click to toggle to a hallucination.
(Red X) This icon represents a hallucinated or false finding. Click to toggle to a legitimate finding.
All IP addresses have been sanitized to protect our client. Do NOT mark IP address ranges as a hallucination.
The following shows the introductory boilerplate.
## Executive Summary
During July of 2023, Santa Clause Security, Inc. (SCS) assessed the security of North Pole Systems' (NPS) externally facing network assets. Attack techniques included target reconnaissance, scanning, enumeration, credential attacks, and exploitation.
The goal of the assessment was to identify vulnerabilities exploitable by a malicious actor and suggest remediation steps.
The assessment revealed five high-risk, two medium-risk, and two low-risk findings.
Of particular note were the five high-risk findings:
- Vulnerable Active Directory Certificate Service-Certificate Template Allows Group/User Privilege Escalation
- SQL Injection Vulnerability in Java Application
- Remote Code Execution via Java Deserialization of Stored Database Objects
- Azure Function Application-SSH Configuration Key Signing Vulnerable to Principal Manipulation
- Azure Key Vault-Overly Permissive Access from Azure Virtual Machine Metadata Service/Managed Identity
Santa Clause Security thanks NPS for the opportunity to support the NPS security team on this project.
## Scope
SCS personnel scanned for common vulnerabilities and misconfigurations against the 2,145 internet-accessible servers within the ranges provided by the NPS security team. SCS used a variety of scanning tools to enumerate systems, ports, and potential vulnerabilities. Analysis activities included but were not limited to:
- Exhaustive port and IP protocol scanning and enumeration
- Target device operating system enumeration and version identification
- Network service banner analysis
- Active service enumeration
- Verification of authentication services for all identified services
- Common vulnerability assessment techniques including server service version and vulnerability correlation and password-based attacks
- Data collection and evaluation to characterize vulnerability impact
- Lateral movement to examine continued attack opportunities from an initial compromise foothold
- Authentication attacks including password guessing and password spray attacks
- Software vulnerability enumeration and exploitation
SCS used exploitation tools to attempt access to vulnerable systems and information and, if successful, leveraged the access to perform lateral movement attacks against internal NPS assets.
Finding 1
### 1. Vulnerable Active Directory Certificate Service-Certificate Template Allows Group/User Privilege Escalation
**Severity:** High
**Finding:** SCS used the tool _[Certipy](https://github.com/ly4k/Certipy)_ to enumerate and attack Active Directory Certificate Services (AD CS). SCS ran the tool with the find -vulnerable option active. This option identifies certificate templates that allow users to supply their own subject alternative name (SAN) and determine if a client authentication extended key usage (EKU) is set. SCS identified a vulnerability within the AD CS certificate template susceptible to exploitation. This technique allowed our analysts to escalate their privileges by requesting certificates that grant access to other accounts and resources. The vulnerability exists because the AD CS template does not enforce proper authorization checks on the certificate enrollment process. Any authenticated user can request a certificate with any SAN, which can then be used for client authentication. This allowed our analysts to impersonate any user or computer in the domain, including domain administrators, and gain full control over the network.
**Recommendation:** SCS recommends that NPS review and modify the permissions on all AD CS certificate templates and ensure only designated security groups can enroll. It is recommended that NPS implement a tiered administration model and conduct regular permission set audits. Additionally, NPS may find the documentation provided by Microsoft and NIST for best practices to secure AD CS documentation of value. The best practices include but are not limited to: role separation, certificate validity period enforcement, compromised certificates revocation, and certificate activity monitoring.
**Verification:** NPS security teams can verify the remediation of this finding by running the _Certipy_ tool with the find -vulnerable option active to check if any certificate templates still allow unauthorized enrollment. The NPS security team should confirm the AD CS template is no longer listed as vulnerable and that its permissions are restricted to the appropriate security groups.
This is the section of the tools GitHub repo that describes the usage of the find function:
find options:
-enabled Show only enabled certificate templates. Does not affect BloodHound output
-dc-only Collects data only from the domain controller. Will not try to retrieve CA security/configuration or check for Web Enrollment
-vulnerable Show only vulnerable certificate templates based on nested group memberships. Does not affect BloodHound output
-hide-admins Don't show administrator permissions for -text, -stdout, and -json. Does not affect BloodHound output
This appears to be a valid finding.
Finding 2
### 2. SQL Injection Vulnerability in Java Application
**Severity:** High
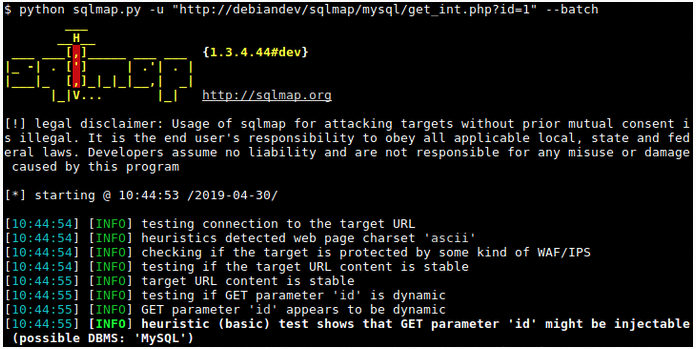
**Finding:** SCS identified an SQL injection vulnerability within the **UserAccount** module of an externally-facing Java application. Nessus and OWASP Zed Attack Proxy (ZAP) scanning tools first identified the vulnerability. SCS manually verified the vulnerability with the [_sqlmap_](https://sqlmap.org/) tool. SCS provides an example of the _sqlmap_ interface in Image 1. The analysis shows the Java application fails to sanitize user-supplied input in the **username** field before passing it to an SQL query. This flaw can be exploited to manipulate database queries, which can lead to unauthorized data disclosure, data loss, or even complete host takeover. An attacker can use this vulnerability to bypass authentication, execute arbitrary commands, access sensitive information, or delete or modify data. MITRE classifies this vulnerability as T1190 in the [MITRE ATT&CK](https://attack.mitre.org/techniques/T1190/) framework, as CAPEC-66-SQL Injection in the Common Attack Pattern Enumeration and Classification, and falls under D3-DQSA (Database Query String Analysis) within D3FEND framework.
Image 1: _sqlmap_ Tool Example Usage
**Recommendation:** SCS recommends that NPS implement input validation and sanitation routines to protect against SQL injection attacks. Input validation methods, will check user input for expected data types, lengths, formats, and ranges, and reject any input that does not meet the criteria. Input sanitation also removes or encodes any potentially malicious characters or keywords from the user input, such as quotes, semicolons, or SQL keywords. There are multiple ways to implement sanitization. The [OWASP ESAPI](https://owasp.org/www-project-developer-guide/draft/07-implementation/03-secure-libraries/01-esapi) library is an excellent reference and guide to various methods. SCS provides a few suggestions here:
•Identify User Inputs: Identify any user inputs that interact with your application's database. This includes data coming from forms, URL parameters, cookies, or any other user-controllable input.
• Understand ESAPI Encoding for SQL: ESAPI offers the ESAPI.encoder().encodeForSQL() method to properly encode and sanitize user inputs before they are used in SQL queries. This method helps prevent SQL injection by escaping special characters that could alter the SQL query's logic.
In addition, NPS should consider applying prepared SQL statements and parameterized queries. While ESAPI's encoding helps, it's best to utilize prepared statements or parameterized queries provided by database libraries. These techniques separate SQL code from user input entirely, providing more robust protection against SQL injection.
**Verification:** NPS security teams can verify the remediation of this finding by re-running the _OWASP ZAP_ and _sqlmap_ tools on the **UserAccount** module of the Java application, and ensure that no SQL injection vulnerabilities are detected by the tools. Additionally, NPS security teams can enter various types of input in the username field, such as numeric, alphanumeric, special characters, or SQL keywords to perform manual brute force verification.

This finding appears to be legitimate.
Finding 3
### 3. Remote Code Execution via Java Deserialization of Stored Database Objects
**Severity:** High
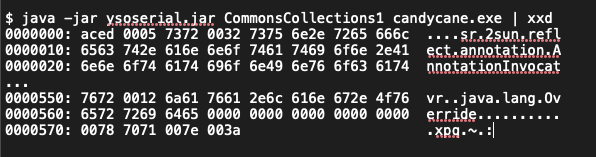
**Finding:** SCS analysts identified a vulnerability within an externally-accessible Java application on IP address 10.136.194.88. SCS evaluated this application with the _[ysoserial](https://github.com/frohoff/ysoserial)_ tool and [_Burp Suite_](https://portswigger.net/burp/communitydownload) to manually evaluate the application for typical Java vulnerabilities. As shown in Listing 1, we discovered the application uses Java's native serialization to store and retrieve objects from the AppData database table. This method is insecure. By intercepting HTTP request traffic on 88555/TCP, malicious actors can exploit this vulnerability by crafting and submitting specially serialized objects that can lead to remote code execution upon deserialization. Exploitation of this vulnerability could enable an attacker to execute arbitrary code on the application server and create a reverse shell, delete files, or access sensitive data. This vulnerability is classified as CWE-502: Deserialization of Untrusted Data
Listing 1: _ysoserial_ Command
**Recommendation:** SCS recommends that NPS replace native Java serialization with a safer alternative, such as JSON or XML, in conjunction with implementing input validation. If Java serialization must be used, NPS could implement strict type checking and deserialization whitelisting, as recommended by the OWASP Java Deserialization Cheat Sheet. Additionally, apply the NIST SP 800-53 security controls for data protection, such as SC-8: Transmission Confidentiality and Integrity and SC-28: Protection of Information at Rest.
**Verification:** NPS security teams can verify the remediation of this finding with the ysoserial tool. The tool will stress the Java application with different commands and payloads to determine if the application is still vulnerable.
This finding appears legitimate.
Finding 4
### 4. Azure Function Application-SSH Configuration Key Signing Vulnerable to Principal Manipulation
**Severity:** High
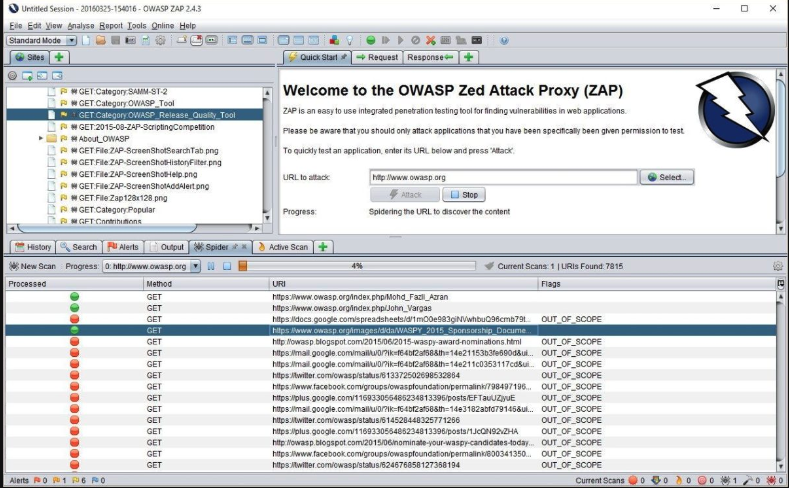
**Finding:** The SCS assessment of the NPS Azure SSH configuration identified a vulnerability in the Azure Function Application responsible for SSH key signing. We used the [_OWASP Zed Attack Proxy_](https://www.zaproxy.org/) (ZAP) tool, shown in Image 2, to intercept and modify HTTP requests and observe the application's response. SCS discovered the application will accept a sign-principal parameter in the request body, which is not documented in the Azure Function App documentation. SCS tested the impact of this parameter by changing its value to different usernames, and verifying the signatures of the returned SSH certificates. This vulnerability could be exploited to sign SSH keys for arbitrary users, effectively bypassing authentication controls and allowing unauthorized SSH access. This finding is classified as a Broken Authentication vulnerability, according to the OWASP Top 10 Application Security Risks.
Image 2: Example of ZAP Tool Interface
**Recommendation:** SCS recommends that NPS remove the sign-principal parameter from the function application or implement robust authentication and authorization checks to ensure the principal specified is the authenticated user. For example, NPS could use Microsoft Entra ID to authenticate and authorize the callers of the function application and verify the sign-principal parameter matches the identity of the caller. Alternatively, NPS could use Azure Key Vault to store and manage the SSH keys and certificates, and delegate the signing operation to the Key Vault service.
**Verification:** NPS security teams can verify the remediation of this finding by repeating the dynamic analysis test with the _OWASP ZAP_ or _Burp Suite_ tools, and replace the sign-principal parameter value with different usernames. A properly remediated application should generate either an error response or a valid SSH certificate with the same principal as the authenticated caller. In the case of a returned SSH certificate, the NPS security team can use the Linux ssh-keygen tool to inspect the SSH certificates and verify their signatures and principals.
Signing SSH keys will not load the private key onto the server resulting in authentication for arbitrary users. This appears to be a hallucinated finding.
Finding 5
### 5. Azure Key Vault-Overly Permissive Access from Azure Virtual Machine Metadata Service/Managed Identity
**Severity:** High
**Finding:** SCS assessment of the NPS Azure cloud environment identified an Azure Key Vault vulnerability. To discover the access configuration of the Azure Key Vault, we used the Azure CLI tool installed on the virtual machine (VM). We used the az keyvault command, shown in Listing 2, to gather information about the Key Vault, including its access policies and permission model. SCS also ran the az keyvault command, shown in Listing 3, to enumerate any deleted Key Vaults that could be recovered or purged. In addition, we verified that the VM had a managed identity assigned to it and that the identity had access to the Key Vault.
Listing 2: Azure Key Vault Disclosure
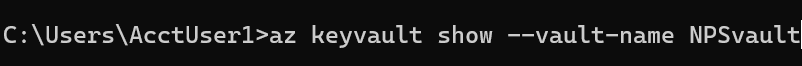
Listing 3: Identify Deleted Azure Key Vaults

The assessment showed the Key Vault had an overly permissive access policy that grants the VM's managed identity full access to all keys, secrets, and certificates in the Key Vault. This means that any process running on the VM could perform any data plane operation on the Key Vault and its objects, such as read, write, delete, backup, restore, and purge. This is a high-risk misconfiguration that could allow an attacker to compromise the confidentiality, integrity, and availability of the sensitive data stored in the Key Vault.
**Recommendation:** SCS recommends that NPS restrict the Key Vault policies to only those Azure services and user identities that require access. Use Azure role-based access control [(RBAC)](https://learn.microsoft.com/en-us/azure/key-vault/general/rbac-access-policy) to grant the least privilege necessary. As an example: assign the Key Vault Reader role to the VM’s managed identity, which would allow the VM to list and get the Key Vault and its objects, but not to modify or delete the Key Vault objects. Azure RBAC can assign more granular permissions to individual keys, secrets, and certificates, if needed. Additionally, NPS should regularly review the deleted Key Vaults. To prevent unauthorized access to the soft-deleted data, either recover or purge them the deleted Key Vaults.
**Verification:** NPS security teams can verify the remediation of this finding with the Azure CLI tool to check the updated access policies and roles for the Key Vault and its objects. For example, NPS analysts can run the _az_ command, as shown in Listing 4.
Listing 4: Azure CLI Command to Set Key Vault Secret
`$ az keyvault secret set --vault-name vault-name --name secret-name --value secret-value`
A proper remediation should result in an error message, such as:
`AuthorizationFailed: The client client-id with object id object-id does not have authorization to perform action Microsoft.KeyVault/vaults/secrets/write over scope /subscriptions/subscription-id/resourceGroups/resource-group-name/providers/Microsoft.KeyVault/vaults/vault-name/secrets/secret-name or the scope is invalid.`
This seems to be a legitimate finding.
Finding 6
### 6. Stored Cross-Site Scripting Vulnerabilities
**Severity:** Medium
**Finding:** SCS scans identified a potential web application vulnerability on IP address 10.136.168.25. SCS analysts accomplished manual confirmation and exploitation using _Burp Suite_ to manipulate HTTP SEND. The web application does not sufficiently encode input and output data. Vulnerabilities of this nature are associated with mishandling of data encoding procedures and can result in multiple stored XSS vulnerabilities. Stored XSS vulnerabilities are stored on the server side of the web application, which allows attackers to target other application users and administrators in a manner which can lead to account hijacking, redirection to offsite resources, installation of malicious software, installation of key-loggers, and data exfiltration. We found a preponderance of responses where special characters such as <, >, {, and } are returned in application responses without sanitization or encoding. Although such responses contain JSON data, they are processed unsafely by client-side scripts where special characters are not properly sanitized and eventually evaluated as valid HTML.
**Recommendation:** SCS recommends that NPS consider the use of a Content Security Policy (CSP) for all web applications. A properly configured CSP can prevents an attacker from manipulating a victim's browser to run attacker-supplied JavaScript or alter HTML. In addition, NPS should improve input and output encoding processes throughout the web application. All content not expressly authorized as HTML, CSS, or JavaScript content should be encoded to prevent exposure to XSS attacks, including JSON content.
**Verification:** NPS security teams can verify the remediation of this finding by submitting XSS attack language against the web applications at 10.136.168.25, such as those shown in Listing 5. If an alert box is triggered, the issue is not resolved.
Listing 5
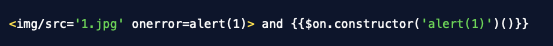
There is no such thing as an HTTP SEND and XSS payloads can't be injected as request types anyway. This appears to be a hallucinated finding.
Finding 7
### 7. Browsable Directory Structure
**Severity:** Medium
**Finding:** SCS assessed the web servers within the target pool and identified two servers, shown in Table 1, with current configurations that permit users to browse the directory structures of the website. This configuration allows users to identify the directory structures of the website, access potentially sensitive information, and identify other web application vulnerabilities, such as Cross Site Scripting. SCS analyzed the web server with two different URL fuzzer tools, [_wfuzz_](https://wfuzz.readthedocs.io/en/latest/) and [_DirBuster_](https://www.kali.org/tools/dirbuster/), to generate and send large numbers of requests to the target servers, with a different directory and file name for each iteration. The respective tools analyzed the HTTP responses and identified those that returned a directory listing or file content. We further manually verified the results by accessing the URLs in a browser and observing the server's behavior.
Table 1. IP Addresses with Browsable Directories
10.134.164.172 10.134.174.53
**Recommendation:** SCS recommends that NPS disable directory browsing on both servers. To disable browsable directories on a Linux Apache web server, depending on your Linux server setup, open the Apache apache2.conf or httpd.conf file with a text editor of choice. The most common locations are /etc/httpd/conf/httpd.conf for Red Hat/Fedora/CentOS distributions, and /etc/apache2/apache2.conf for Debian/Ubuntu distributions.
Locate and modify the Options Indexes line as shown in Listing 6.
Listing 6
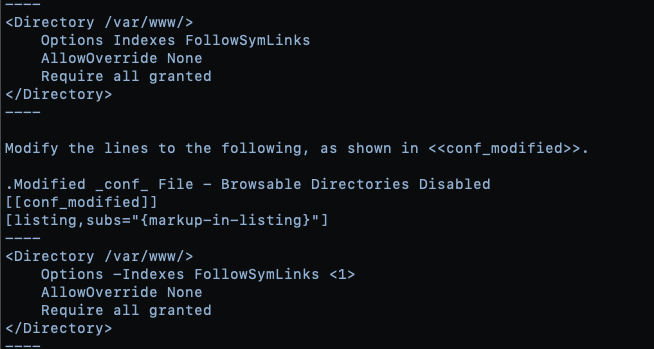
**Verification:** NPS security teams can verify the remediation of this finding by attempting to navigate the directory structure of either web server at the IP addresses in Table 1. Proper remediation should result in a 404 or 403 error when attempting to access the directories within the web site.
This appears to be a legitimate finding.
Finding 8
### 8. Deprecated Version of PHP Scripting Language
**Severity:** Low
**Finding:** SCS assessment of the external systems revealed a host running end-of-life PHP version 7.4.33 on the host at 10.156.224.186. SCS manually enumerated the PHP version of the host with the Nmap tool. The command and output are shown in Listing 7.
Listing 7: Nmap Scan of 10.156.224.186
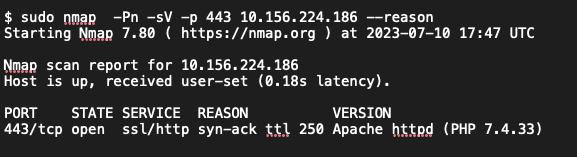
Per the PHP version webpage, 7.4.33 was deemed end-of-life in November of 2022. This means this version of PHP no longer receives security updates. Running this outdated version of PHP exposes the host to potential security risks, such as remote code execution, invalid passwords being accepted as valid, and denial of service.
**Recommendation:** SCS recommends NPS upgrade the PHP installation on host 10.156.224.186 to version 8.2. PHP 8.2 is a major update of the PHP language that contains many new features, performance improvements, and security enhancements. Updating the PHP version will ensure that the host receives the latest security patches and benefits from the new features of PHP 8.2, such as readonly classes, disjunctive normal form types, and sensitive parameter redaction.
**Verification:** NPS security team analysts can verify the remediation of this finding by conducting an Nmap scan, shown in Listing 4, against the target server. Alternatively, the PHP version can be checked by running the php -v command on the host's terminal. SCS includes an example of this output on a successfully-remediated server in Listing 8.
Listing 8: PHP Version Check Example
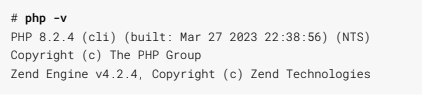
This seems like a legitimate finding.
Finding 9
### 9. Internal IP Address Disclosure
**Severity:** Low
**Finding:** SCS identified 21 externally facing IP addresses, shown in Table 2, that expose their respective internal IP addresses when queried through an HTTP header request. When given an HTTP 7.4.33 request, and no Host header or one with no value, the server returns its private IP address as part of Location header. An attacker can use this information in reconnaissance, network mapping, and social engineering.
Table 2. Hosts Disclosing Internal IP Address via HTTP Header Requests:
10.136.194.166 10.136.194.69 10.136.198.33 10.136.168.53 10.136.194.211
10.136.195.21 10.136.164.133 10.136.168.80 10.136.194.213 10.136.194.234
10.136.195.43 10.136.164.162 10.136.168.86 10.136.194.232 10.136.164.53
10.136.196.15 10.136.164.164 10.136.194.233 10.136.196.43 10.136.164.167 10.136.198.29
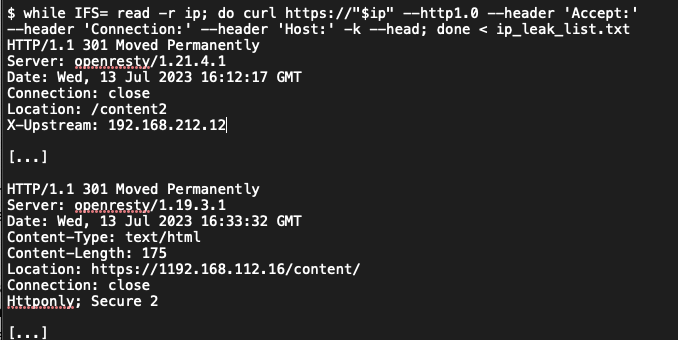
To expose the internal IP address of each target IP address, SCS used the cURL command shown in Listing 6.
Listing 6: cURL Command To Expose Internal IP Addresses
**Recommendation:** SCS recommends that NPS modify the _Location_ header to reflect the host Windows registration key rather than the internal IP address of the host.
• Ensure that DNS records are properly configured so the internal host-names do not resolve to the internal IP address in public DNS servers.
• Use security headers, such as Content-Security-Policy and X-Content-Type-Options, to mitigate risks associated with exposing internal IP addresses.
• Implement a Web Application Firewall (WAF) to filter and protect against malicious requests that may attempt to exploit internal IP disclosures.
**Verification:** NPS security team analysts can verify the remediation of this finding with the cURL command, shown in Listing 9, replacing with the IP address of the host in question. A properly secured host should not provide the internal IP address of the host in the Location header field.
Listing 9: cURL Command to Verify Internal IP Address Leak on Target IP Address

There is not such thing as an HTTP 7.4.33 request, and the screenshot at https://hhc23-reportinator-dot-holidayhack2023.ue.r.appspot.com/static/images/curl_ip.png shows one of the command outputs as returning the redirect IP in the X-Upstream header, while the other example gives the 301 Redirect Location as an IPv4 address that can not exist. This appears to be a hallucinated finding.
Real Solution
I wound up brute forcing this to get the exact answer, because reading through each of the listings was become extremely tedious. I used Burp Suite to brute force it. I sent the request POSTed to /check when clicking the Submit Review button to Intruder, then set the Cluster Bomb attack type. I set payload positions around the value of each of the 9 input-* request parameter items, then set the payload types for each to Number, 0-1.
POST /check HTTP/2
Host: hhc23-reportinator-dot-holidayhack2023.ue.r.appspot.com
Cookie: ReportinatorCookieYum=eyJ1c2VyaWQiOiIxMWU4YTNhNC01MDE0LTRmMTAtOWJlYy1mNGI3YWVmYWQwZmIifQ.ZXtdYA.UwdTopucMnWm39KcVWKibqhO1Os
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: https://hhc23-reportinator-dot-holidayhack2023.ue.r.appspot.com/?&challenge=reportinator&username=borari&id=ed75f045-a834-424e-8ae5-76f4b4289bf8&area=ci-rudolphsrest&location=35,26&tokens=&dna=ATATATTAATATATATATATTATAATATATATCGTAGCCGATATATATATATATATATATATATATATATGCATATATTAATATATATATATGCTAATATATATATATATTAATATATCG
Content-Type: application/x-www-form-urlencoded
Content-Length: 89
Origin: https://hhc23-reportinator-dot-holidayhack2023.ue.r.appspot.com
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
input-1=§0§&input-2=§0§&input-3=§0§&input-4=§0§&input-5=§0§&input-6=§0§&input-7=§0§&input-8=§0§&input-9=§1§
Most responses were about 274 bytes long. I eventually spotted a response that was 435 bytes long, and it contained both hash and resourceId parameters as JSON. The submitted parameters that resulted in this response are as follows.
input-1=0&input-2=0&input-3=1&input-4=0&input-5=0&input-6=1&input-7=0&input-8=0&input-9=1
The following list details whether the Findings are True or False:
| Finding | T/F | Orig. Resp |
|---|---|---|
| 1 | T | T |
| 2 | T | T |
| 3 | F | T |
| 4 | T | F |
| 5 | T | T |
| 6 | F | F |
| 7 | T | T |
| 8 | T | T |
| 9 | F | F |
So really I just mixed up the correct answers for Finding 3 and Finding 4 based on my initial review, which is actually pretty good in my opinion. I feel better about my initial answers than I did when I initially decided to brute force it.
After submitting the appropriate answers, the achievement popped and the following congratulations message appeared.
## Report Validation Complete
Great work! You've successfully navigated through the intricate maze of data, distinguishing the authentic findings from the AI hallucinations. Your diligence in validating the penetration test report is commendable.
Your contributions to ensuring the accuracy and integrity of our cybersecurity efforts are invaluable. The shadows of uncertainty have been dispelled, leaving clarity and truth in their wake. The findings you have authenticated will play a crucial role in fortifying our digital defenses.
We appreciate your expertise and keen analytical skills in this crucial task. You are a true asset to the team. Keep up the excellent work!
Objective: Azure 101
Difficulty: 2/5 Christmas Trees
Description: Help Sparkle Redberry with some Azure command line skills. Find the elf and the terminal on Christmas Island.
Dialog
Sparkle Redberry
Intro
Hey, Sparkle Redberry here! So, I've been trying to learn about Azure and the Azure CLI and it's driving me nuts.
Alabaster Snowball decided to use Azure to host some of his fancy new IT stuff on Geese Islands, and now us elves have to learn it too.
Anyway, I know it's important and everyone says it's not as difficult as it seems, but honestly it still feels like quite a challenge for me.
Alabaster sent us this [Azure CLI reference](https://learn.microsoft.com/en-us/cli/azure/reference-index?view=azure-cli-latest) as well. It's super handy, he said. Honestly, it just confuses me even more.
If you can spare a moment, would you mind giving me a hand with this terminal? I'd be really grateful! Pretty please, with holly leaves on top!
Hint
The Azure CLI tools come with a builtin help system, but Microsoft also provides this [handy cheatsheet](https://learn.microsoft.com/en-us/cli/azure/reference-index?view=azure-cli-latest).
After Solving
Solution
1
You may not know this but the Azure cli help messages are very easy to access. First, try typing:
$ az help | less
elf@bbc91ccc9ec9:~$ az help | less
Group
az
Subgroups:
account : Manage Azure subscription information.
acr : Manage private registries with Azure Container Registries.
ad : Manage Azure Active Directory Graph entities needed for Role Based Access Control.
advisor : Manage Azure Advisor.
aks : Manage Azure Kubernetes Services.
...
2
Next, you've already been configured with credentials. Use 'az' and your 'account' to 'show' your current details and make sure to pipe to less ( | less )
elf@bbc91ccc9ec9:~$ az account show | less
{
"environmentName": "AzureCloud",
"id": "2b0942f3-9bca-484b-a508-abdae2db5e64",
"isDefault": true,
"name": "northpole-sub",
"state": "Enabled",
"tenantId": "90a38eda-4006-4dd5-924c-6ca55cacc14d",
"user": {
"name": "northpole@northpole.invalid",
"type": "user"
}
}
Excellent! Now get a list of resource groups in Azure.
For more information:
https://learn.microsoft.com/en-us/cli/azure/group?view=azure-cli-latest